Multi-Factor Authentication (MFA)
MFA Advantages
You can enhance the security of your e-INFRA CZ Account by enabling Multi-Factor Authentication (MFA). MFA adds an additional verification step during login, making unauthorized access significantly harder. Some services in the e-INFRA CZ infrastructure require MFA to be enabled.
The e-INFRA CZ AAI (Authentication and Authorization Infrastructure) supports two MFA methods:
- TOTP (Time-based One-Time Password)
- WebAuthn (Web Authentication, button press, fingerprint, etc.)
Check our interactive guide to help you choose the right MFA method based on your device and preference.
TOTP (Time-based One-Time Password) Setting
TOTP is a widely used standard where a mobile or desktop app generates 6-digit codes that change every 30 seconds. These codes are generated based on a shared secret between your device and our servers.
Also Known As
You might recognize TOTP under other names such as:
- Verification code
- Authenticator code
- 6-digit code from code generator or Google Authenticator
- Code from authentication/verification app
- Works across multiple platforms (PC, mobile, tablet)
- Compatible with many authenticator apps
- Offline capable (no need for an internet connection)
Supported Apps
Choose any of the following TOTP-compatible apps:
Or use the TOTP functionality built into password managers:
If you already use a TOTP app, simply add your e-INFRA CZ account. No need to install another.
TOTP is standardized in RFC 6238
WebAuthn (Web Authentication) Setting
WebAuthn is often integrated into modern operating systems and browsers.
In order to use WebAuthn, you need to use one of the supported web browsers together with the operating system capability, an app or a physical authenticator (e.g. a YubiKey).
- A hardware token (e.g. YubiKey)
- No codes to type — just confirm with your device (button press, fingerprint, etc.)
- Built into many devices and platforms
- Extremely secure against phishing and account takeover
- Built-in platform authentication (e.g. Windows Hello, macOS Touch ID)
Also Known As
WebAuthn may also appear under other names like:
- FIDO2
- U2F (Universal 2nd Factor)
- Security key
- USB security key Learn more at webauthn.io and webauthn.me.
WebAuth Support in various OS
- Windows 10+: Use Windows Hello using a PIN, facial recognition, or fingerprint. Windows 10 build 1903 or later is required.
- macOS 10.15+: Touch ID feature can be used (Chrome, Safari).
- Android 7+: Requires screen lock (PIN, pattern, fingerprint, face)
- iOS 14.5+: Touch ID / Face ID
- Linux: Use USB-based FIDO2 tokens (e.g., Yubikey](https://www.yubico.com/authentication-standards/fido2/)) Bluetooth enabled on both devices, Google Chrome browser on both, and the phone to be in close proximity to the PC. If your Android Chrome browser has an authenticated Google Account, screen lock methods can be used for the second factor; otherwise, you can scan a one-time QR code from the PC screen with your phone.
- Alternatively a NFC or USB connected hardware token like Yubikey can be used.
How to Set MFA in Perun
Register at least one token. Your first token must be TOTP.
Once you register your first token, MFA will be required whenever you log in to manage or modify your MFA settings.
Register Your First Token
-
Visit the MFA Management Page, or go to your e-INFRA CZ User Profile and navigate to
Authentication->Multi-Factor Autentication (MFA) -
Click on
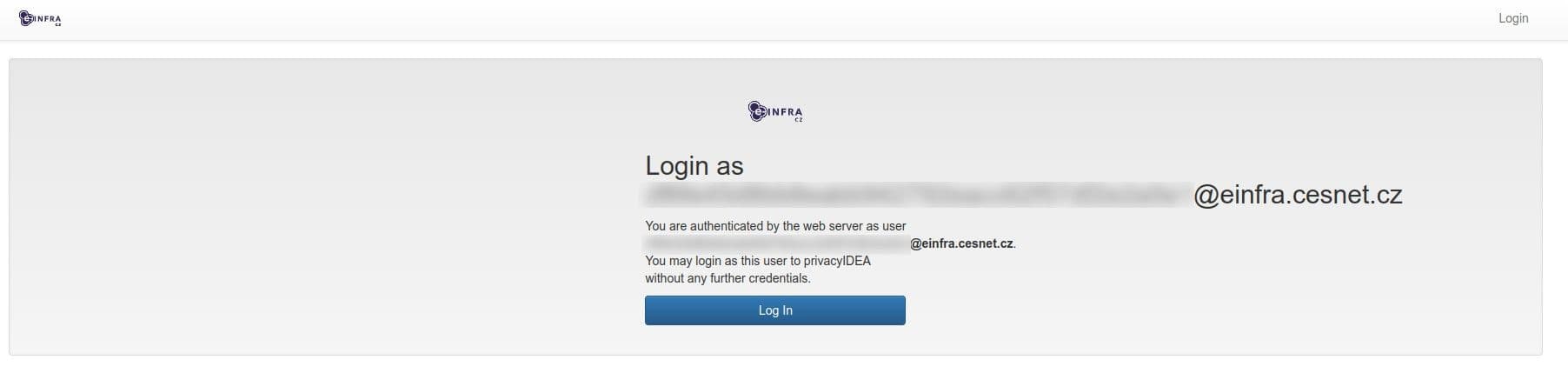
Manage my MFA tokensand sign in with your identity from your home institution. -
Click Log In to enter the MFA management application (privacyIDEA).
-
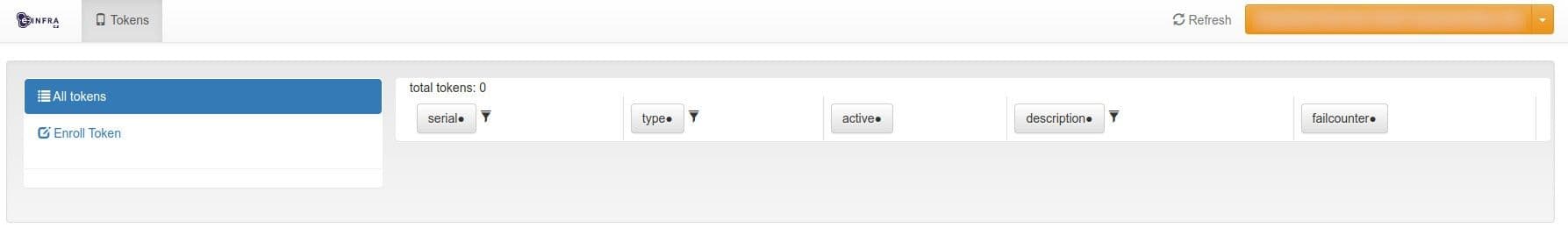
Choose Enroll Token in the left menu
-
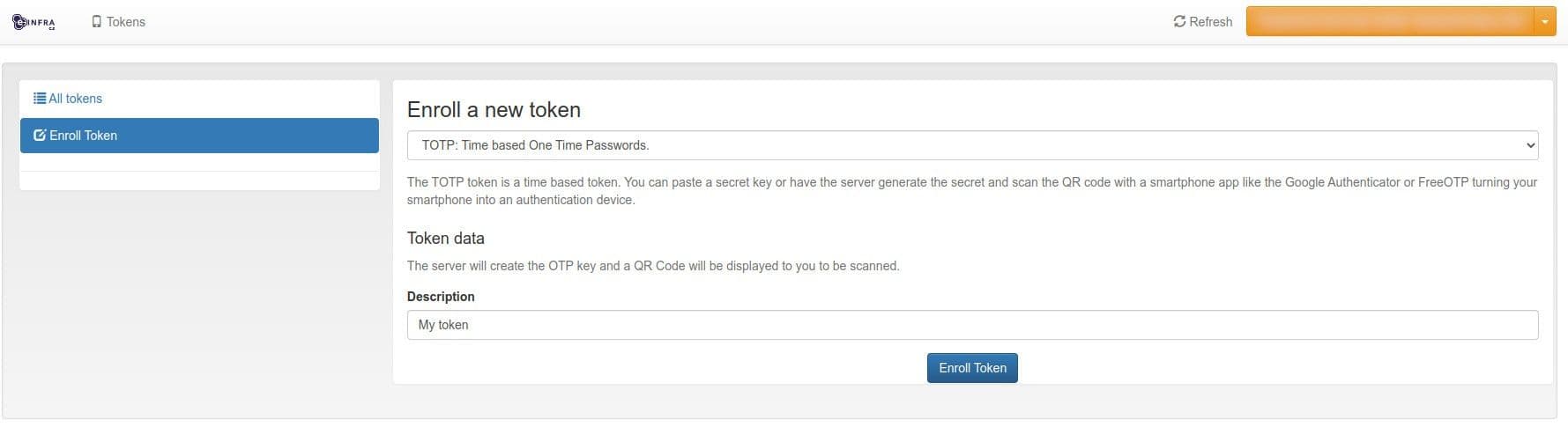
Select TOTP, enter a description, and click Enroll Token.
-
Scan the displayed QR code with your TOTP app.
- If using a mobile device, you can tap the link to open the TOTP app directly.
You can add more TOTP apps later — a new QR code will be generated.
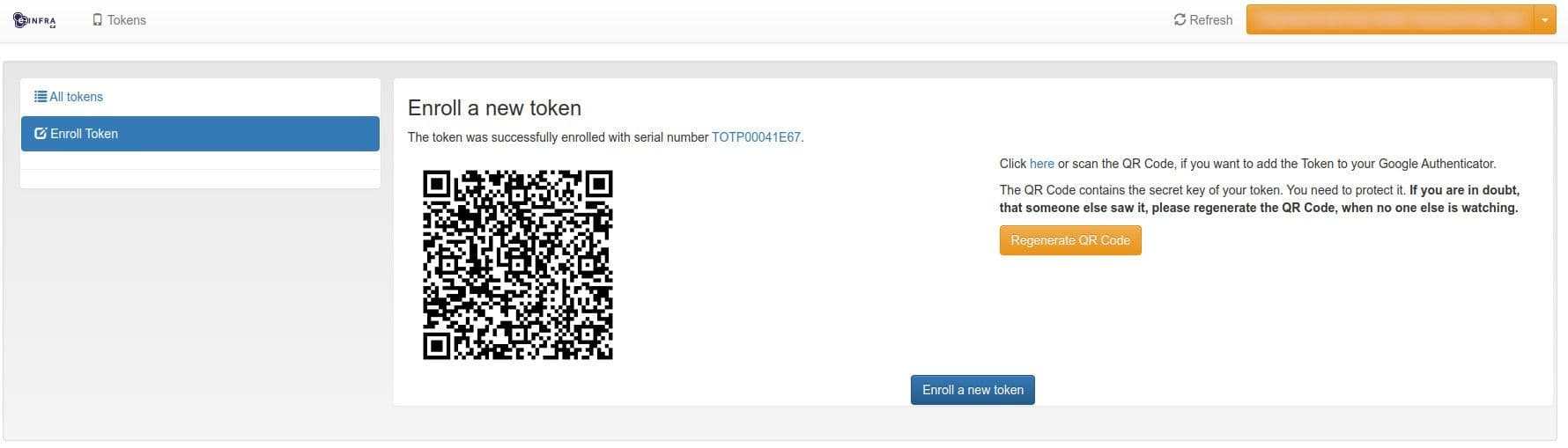
Next time you log in, MFA will be required using this token.
Add More Tokens
-
Click Enroll Token again.
-
Choose WebAuthn (if supported), enter a description, and click Enroll Token.
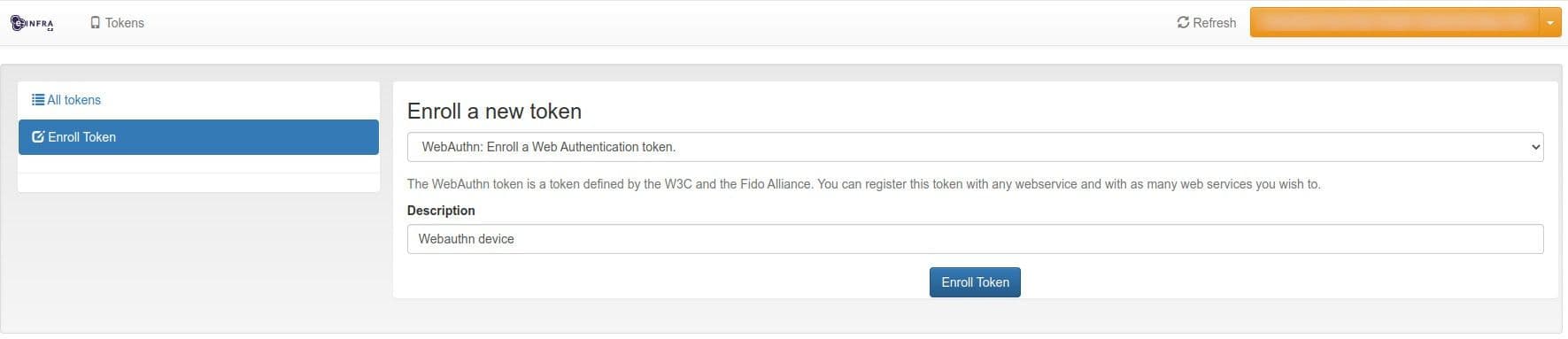
-
Confirm registration using your device (e.g., fingerprint, hardware token).
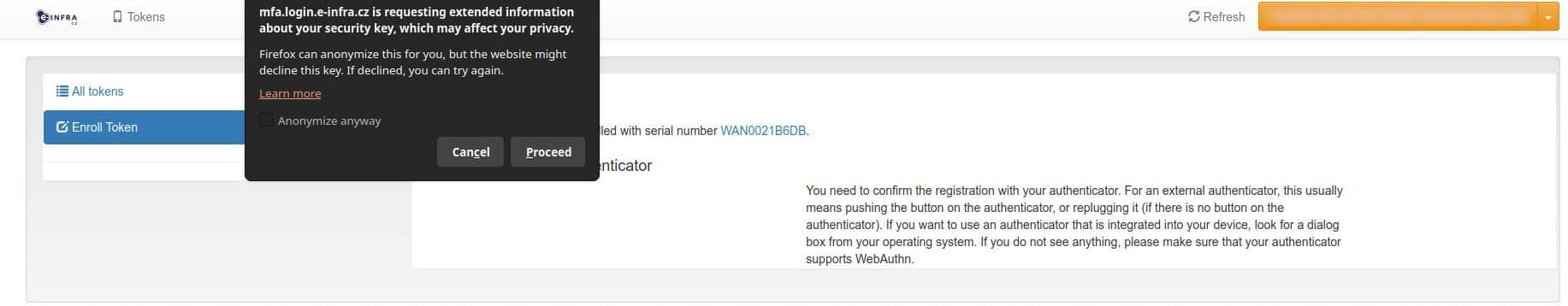
-
After successful registration a confirmation appears.
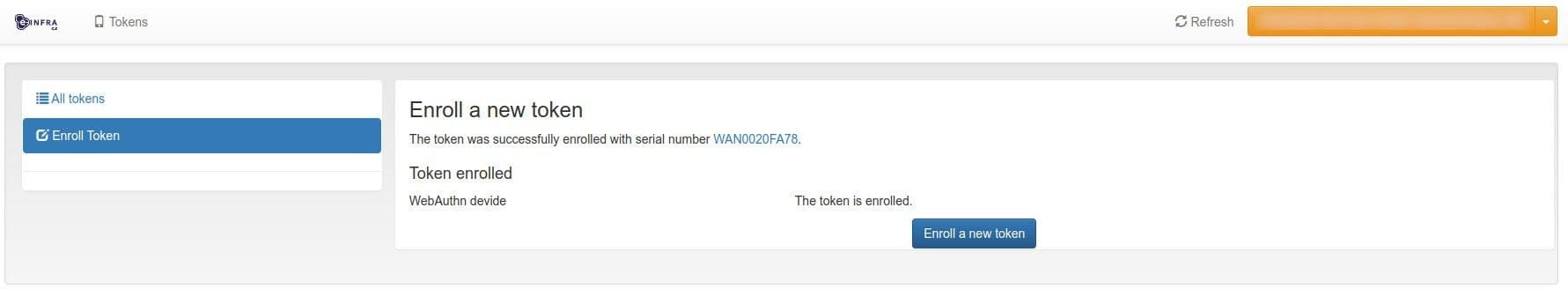
We strongly recommend registering at least two tokens, including one TOTP app, to prevent lockout.
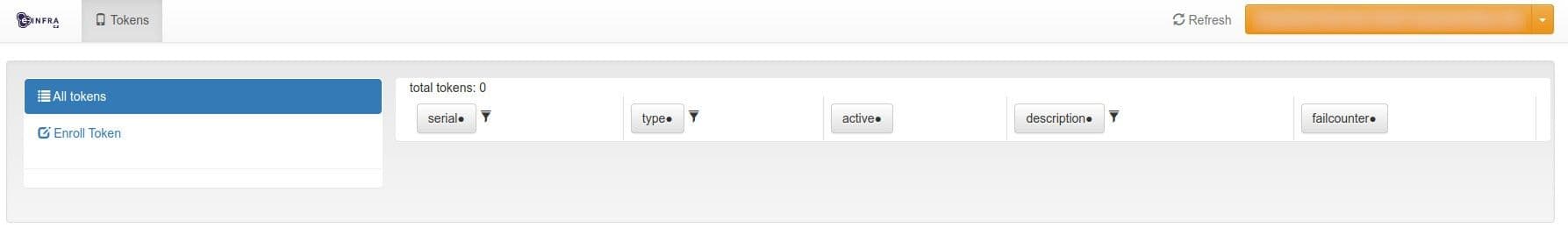
Prepare Recovery Codes
To regain access if you lose all tokens, generate and securely store one-time recovery codes.
-
Click Enroll Token
-
Select
PPR: One Time Passwords printed on sheet of paper, provide a description, and click Enroll Token.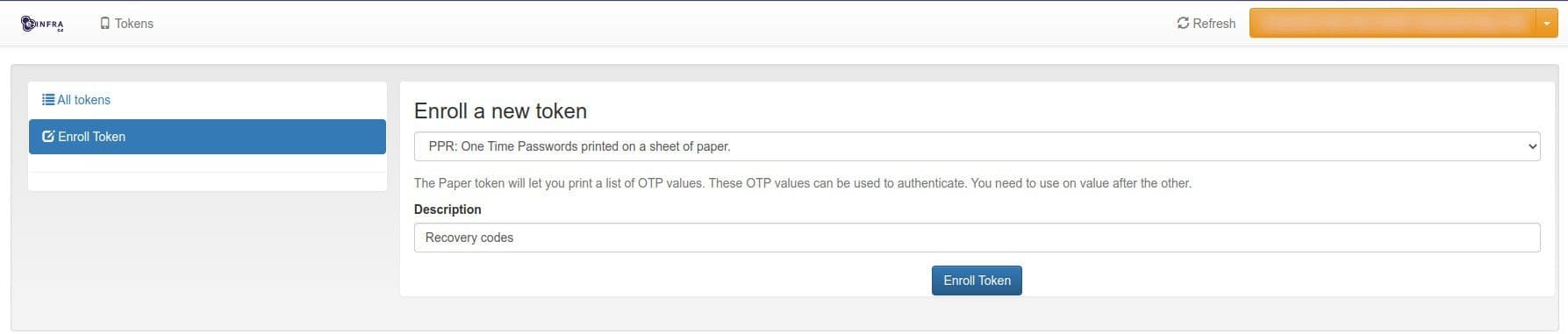
-
View or print the codes by clicking
The OTP ValuesorPrint the OTP list.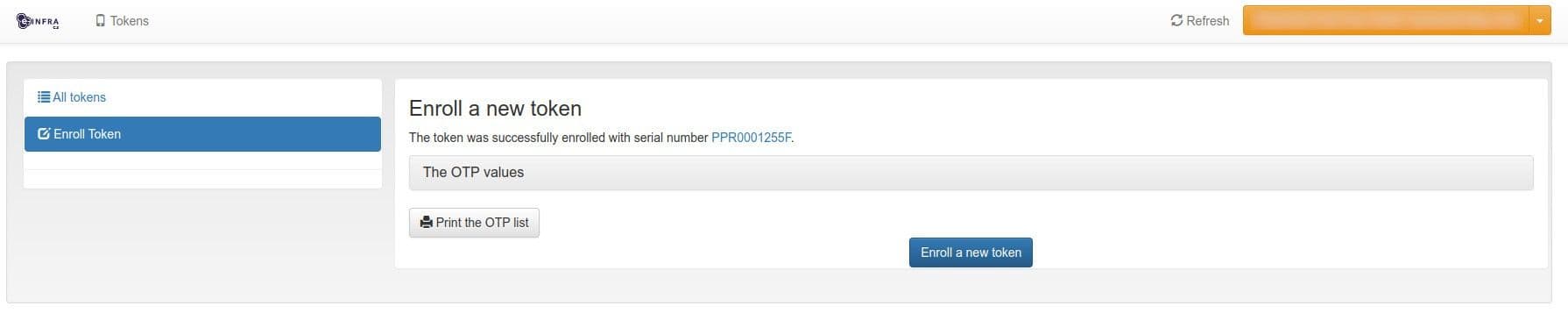
Recovery codes.
To prevent being locked out of your account, we strongly recommend generating one-time recovery codes in case you lose access to your MFA tokens. See the Recovery Codes section for more information.
Enable or Disable MFA for (All) Services
MFA is required:
- If a service mandates it, or
- If you explicitly enable it in your account settings
To enable MFA globally:
- Go to your e-INFRA CZ User Profile
- Navigate to
Authentication->Multi-Factor Autentication (MFA) - Toggle
Turn on multi-factor authentication for all services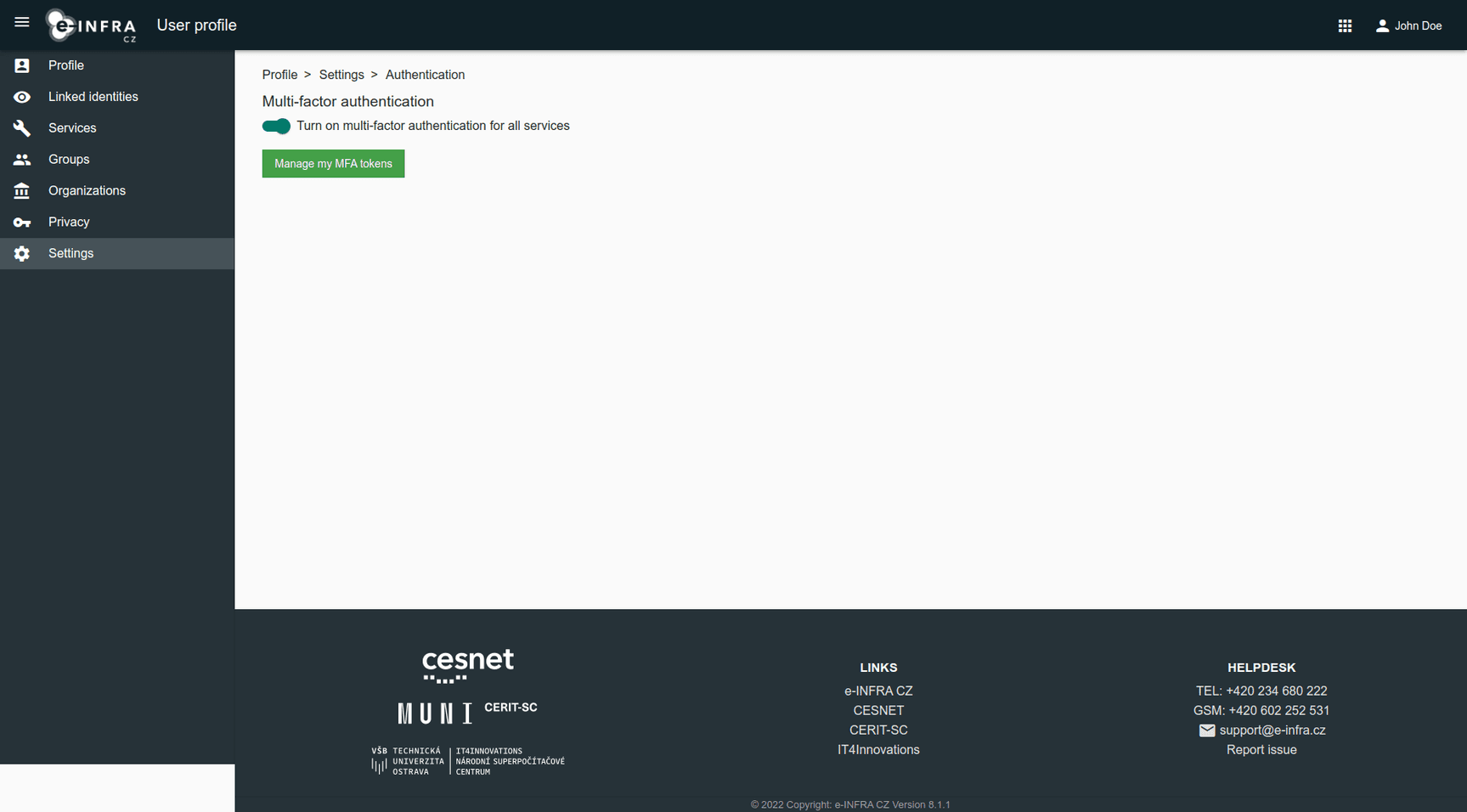
Perform MFA
When Is MFA Required?
- When accessing services that require MFA
- When you enable MFA for all services
- When managing MFA settings or tokens
How to Log in Using MFA
- Log in using your home organization or e-INFRA CZ credentials.
- If MFA is required, you’ll be prompted to verify using TOTP or WebAuthn.

Both options TOTP and WebAuthn are displayed, and you must pick the one based on the type of MFA token you registered and have available at the moment. You can have both types of tokens registered; in such a case, you can choose any of the options.
If you have no valid tokens or authentication fails, you will receive an error message.
MFA with Home Organization Login
If your home institution supports MFA and releases that information during login, you don’t need to repeat MFA within e-INFRA CZ.
Currently, this is supported only by Masaryk University.
Important
You must still register at least one MFA token with your e-INFRA CZ Account to retain access if your affiliation changes.
MFA tokens managed by your home organization are not supported by us, and we cannot assist if you lose access to them.
Do not register shared or employer-owned MFA tokens (e.g., company-issued YubiKeys) unless you are sure they are your personal devices.
Last updated on